Capturing traffic
Capturing traffic is the first step to analyze it. At startup, the proxy is on and client configured manually to use it can intercepted. The state of the proxy is indicated on the bottom right corner of the window.

Fluxzy provides several ways to deflected traffic to the proxy :
- from all OS traffic
- from specific traffic with source filter
- from new instance of browsers and terminals detected on the host OS
Capturing OS traffic
All traffic
To capture all OS traffic, just click on the "Capture" button or from menu Capture > Start recording
Specific traffic
Fluxzy supports exclusive traffic capture by source filtering. Filters that are eligible for source filtering must have a scope of OnAuthorityReceived.
To configure the source filter, you can click on the filter icon in toolbar.

Choose the filter from the dialog box and once the source filter is set, the icon will turn into yellow meaning that the filter is active.

Note: When the source filter is on, other traffic is still traveling through the proxy except that it's directly tunneled to the destination without being intercepted or saved. If you wish to completely avoid this redirection, you can add the corresponding host into by the bypass list (Menu Settings > Proxy Settings > By pass list)
Capturing browsers and shells
Fluxzy can detects browsers and terminals running in the host OS and launch a brand new captured instance. This is useful when you don't want to be disturbed by background OS traffic.
Detected browsers and terminals can be found on the menu Capture > Launch captured application.
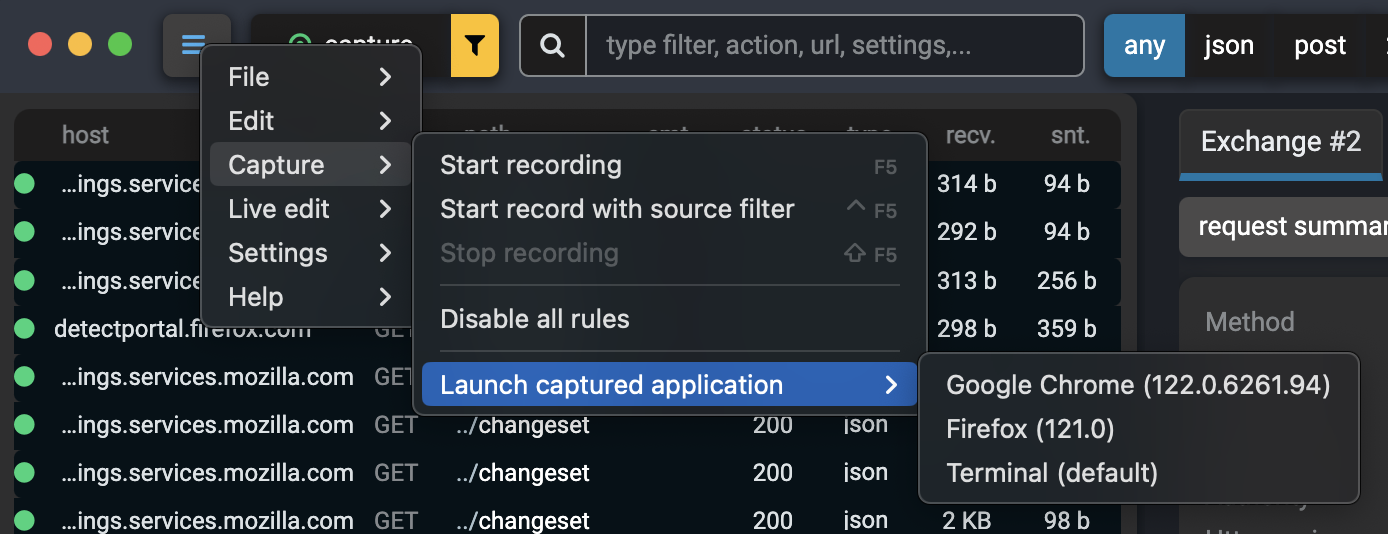
One a captured application is launch, all traffic from the application is intercepted.
Available applications are also directly available from the Search EveryWhere feature.