Connecting devices
1. Introduction
There are two things to consider when connecting devices to Fluxzy:
- The traffic must pass direct to the proxy: The application or device should be configured to send its data traffic through a specified proxy.
- The ROOT certificate must be trusted by client: The application or device must recognize and trust the root certificate provided by Fluxzy. This second constraint can be circumvented by ignoring certificate validation error.
If the application is located on the same machine as the fluxzy instance, you can use OS Traffic deflections and certificate wizard to automatically configure most applications.
- Fluxzy Desktop has a "Launch captured application" feature that will automatically configure the application to use the proxy. Available applications are stock web browsers and main terminal on supported OS.
2. Automatic OS Traffic Deflections
OS Traffic Deflections is a fluxzy feature that will setup automatically the system proxy settings when the capture session is started (and restore the previous settings when the capture session is stopped).
Some applications might not adhere to global proxy configurations, in which case you'll need to configure the application to use the proxy directly.
Additionally, if you wish to exclude or include only some specific traffic with the automatic traffic deflection, you can use source filter which will tunnel-only undesired traffic. Excluded traffic are not captured in Fluxzy Desktop and
source filters is not limited to host/authority option but can be applied to the whole request header content (example: Include only trafic with a specific user-agent).
source filters can be activated through Capture -> Start capture with source filter.
3. Automatic Certificate Installation
If the activated used root certificate is not installed yet, an automatic wizard will be shown.
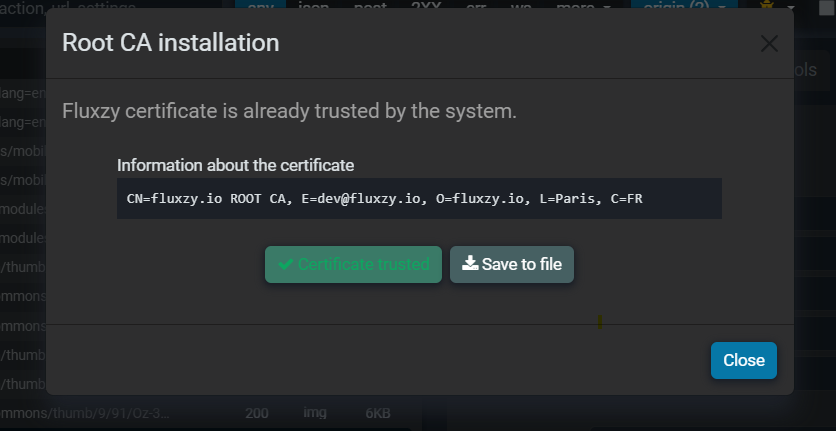
- Certificate installation needs elevation.
Verifying Device Connectivity
When the device is connected to Fluxzy Desktop, the captured exchange will be shown directly on the "exchange panel". However, if you're using a particular view filter, you can verify the connectivity with methods described below.
1. Fluxzy CLI
Fluxzy's command-line interface (CLI) provides a verbose mode using the -v option. This mode displays detailed information about the processed traffic, offering insights into whether a specific device's traffic is being routed through Fluxzy.
When using the CLI in verbose mode, keep an eye out for details related to the device's connection. If Fluxzy captures the device's traffic, it will log its data flow in the output. In case you don't observe the expected logs, you might need to revisit the client or server settings.
2. Browser Certificate Emitter
For devices operating web browsers, you can verify by inspecting the certificate issuer of a browsed website. If your traffic goes through the Fluxzy proxy, Fluxzy should be the certificate issuer for the site you're accessing.
Most browsers permit you to view certificate details by selecting the padlock or security symbol adjacent to the website's URL. From there, navigate to the certificate details and review the issuer. If you find it issued by Fluxzy, your browser's traffic is being correctly directed through the proxy.
3. Fluxzy Verification URL
There are default mounted URL available when running fluxzy in default mode. You can use the to verify that your traffic pass through the proxy.
Fluxzy provides a direct method to ascertain if your device's traffic is passing through its proxy. Simply navigate to either:
- http://localhost:44344: which returns an welcome page
- http://localhost:44344/ca: which returns the public part of currently used ROOT certificate